This article was initially published in the November 2024 newsletter of the SwissICT published.
Traditional security models are increasingly reaching their limits in day-to-day business. Today's collaboration methods and technological developments require adapted cyber security measures.
Cyber security has become much more complex in recent years. The further development of technologies, digital infrastructure and new habits of collaboration are placing new demands on a security organization. Companies and organizations can no longer rely on traditional security models.
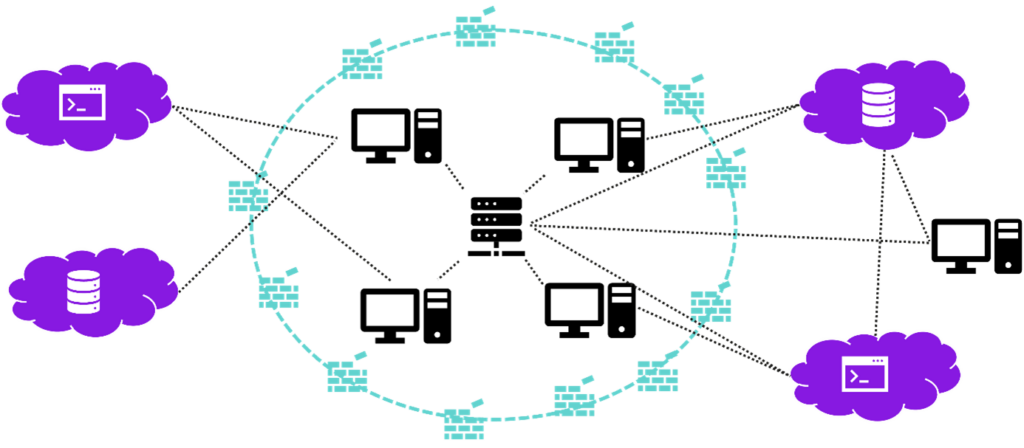
But what are traditional security models? In the past, it was common practice for the network perimeter to be the preferred security tool for protecting against threats and risks. Companies used the network perimeter to build a kind of castle wall around their own organization. Anything that did not need to enter the "castle" for whatever reason was blocked - traditionally by firewalls. Once inside the network perimeter, it was usually possible to move freely in many cases.
Traditional security models are no longer sufficient
Traditional security models have provided very good protection for companies whose data and access to resources have always been within the network perimeter. With the cloud and New Work, however, this solution is no longer up to date. In the cloud, infrastructures, applications and systems are in most cases no longer within the network perimeter, but outside it. Access to resources and data therefore no longer only takes place within the "castle" but also outside it. This turns the concept of the network perimeter as a protection mechanism on its head.
With the newer collaboration models such as "new work", "remote work" or "mobile first", we want to access all data from anywhere, with all kinds of devices. This also contradicts the concept of the castle wall. Traditional security models, which focus primarily on protecting data and resources within the network perimeter, are therefore no longer sufficient.
The necessary mindset change
Cyberattacks, data loss and disruptions to business operations are situations that cannot be completely avoided. The digital world and the infrastructure of many organizations has reached a level of complexity that makes complete control through conventional security measures impossible. For this reason, a change in the understanding of cyber security is also necessary.
Many organizations want to prevent cyberattacks and try to block all potential vulnerabilities. However, in today's digital world, this is almost impossible to do completely. Instead, organizations need to strengthen their resilience to cyberattacks and business disruptions. This means that in addition to preventive measures to prevent attacks and minimize security vulnerabilities, they should prepare themselves to be able to react quickly and limit the damage in the event of an incident. This shifts the focus from purely preventive to more reactive security measures.
What characterizes perimeter-less cybersecurity strategies
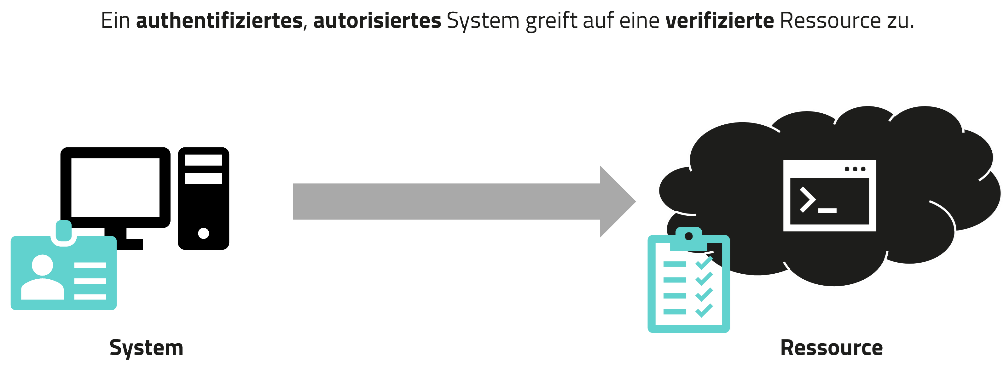
Perimeter-less cyber security strategies are strongly oriented towards the Zero Trust security model. In this case, zero trust is very well suited as a toolbox for using suitable measures and principles and applying them in your own organization. On the one hand, perimeter-less cyber security strategies are about evolving from a network-based to an identity-based approach. Identity plays a central role here: protection no longer takes place at the network perimeter, but at the identity - be it that of the user, the device, the system, the resource or even the data itself. Each element has an identity that can be protected using specific parameters. In this context, access control plays an important role. The corresponding parameters can be used to verify whether a system is allowed to access a resource or not.
Perimeterless cybersecurity strategies should also include organizational aspects to ensure effective protection against cyberattacks. This includes topics such as incident response, emergency processes and business continuity management. These organizational tasks - such as defining responsibilities, developing processes and regularly testing emergency plans - must be clarified and established within the company.